When it comes to digital data, say, on your phone or your computer, it’s not always a viable option to secure it on a piece of paper and store it in a physical vault. That’s where the digital vault services, such as 1Password, LastPass or similar come in handy, but sometimes even those solutions feel awkward. If only there was a solution where I could digitally encrypt my data without having to store it on someone else’s machine…
One solution that could help us solve our dilemma is VeraCrypt. It offers a user friendly way of encrypting our data on our own hardware, without forcing us to involve any third party for the long-term storage purpose (though, we are still perfectly free to store our encrypted “blob” wherever we want to – even our preferred cloud storage provider if we so wish).
A few words on security
Since privacy and security is of utmost importance for us in this example, we will verify the authenticity of the downloaded VeraCrypt installer properly before getting it into our system. For this we will use a GPG (Gnu Privacy Guard) based tool chain.
Worth pointing out is that you don’t have to have any personal digital keys or signatures pre-configured for this. You just need the tools. If you are running a Debian derivative of Linux there is a good chance you already have them pre-installed. In the case of other Linux distributions, or Mac, or Windows, you may have to set it up on your own. Google is your friend here.
Furthermore, if you are involved in a high profile project where there is an imminent risk for being targeted to industry espionage, or you just don’t trust the computer you are working on for any reason, you may even want to take this one step further and set up a Cleanroom environment and access your USB drive through that.
You can of course also choose to skip these extra steps of precaution altogether and jump directly to the Prepare the USB drive section. However, be aware that you are then exposing yourself to a potential attack vector which may or may not be relevant in your case. Think it through and do not rush this decision.
A very brief note on GPG, PGP and keys and signatures
Digital security, encryption and identification are vast topics which would take days, if not weeks, and people far more educated than most of us to explain. A humble attempt is made here trying to give very coarse view of it. If you are really, really interested, the Ubuntu community GPG wiki page could be a good start to learn more.
GPG is short for Gnu Privacy Guard and it is, in it’s simplest form, a tool (a computer program) used to work with digital signatures and keys of a certain type.
PGP is not a typo but short for Pretty Good Privacy and it is a standardised way of calculating and describing the “certain type” of keys used for encryption and signatures. There are several implementations of this standard (RFC4880) where OpenPGP is arguably the most well known and widely spread of them.
Keys and Signatures go way back in time (already-the-ancient-greeks-way-back-in-time). Modern cryptography often relies on key pairs, which is exactly what it suggests: a two-part-key with a private super-secret part which is never ever, under any circumstances what so ever shared with anyone, and one public part which has the exact oposit purpose: to be shared with everyone.
The characteristics and relationship between these two parts is such that what is encrypted with the public key can only be decrypted with the private key and, vice versa; what is encrypted with the private key can only be decrypted with the public key. In reality this is a bit more complex than this, but this is the fundamental geist of it.
The difference between keys and signatures is that while keys are used to ensure privacy, signatures are used to verify authenticity and integrity. It’s the difference between getting or sending a secret message and knowing for sure who sent a message (yes, you can sign un-encrypted messages too).
Again, and I can’t stress this enough; this is barely scratching on the surface of an incredibly large topic. The amount of implications and but’s and however’s are far beyond the scope of this text. It should however give a fair enough understanding of why we at all want to verify the integrity of the VeraCrypt installer.
Verify the integrity of the installation binary
So, now that we know the why, let us get to the how.
Start by downloading the VeraCrypt installer and the corresponding signature file for your platform. Scroll down to the bottom of the download page and also download the SHA-256 and SHA-512 checksum files along with their corresponding signatures. Once you have downloaded all six files, you can open up a Terminal or Console window and try to verify the authenticity of the installer (yes, you need to have a PGP standards compliant tool installed for this, such as GPG):
gpg --keyid-format long --verify <signature> <installer>Oh, good heavens! It failed with an error message because we have not imported the VeraCrypt public key to check the signature with yet:
gpg: Signature made sun 27 okt 2019 18:54:11 CET
gpg: using RSA key 5069A233D55A0EEB174A5FC3821ACD02680D16DE
gpg: Can't check signature: No public keyFor once we are actually happy for this failure, because it reveals information on which public key we need to get in order to verify the signature (5069A233...). We can now try to fetch that key from a trusted, public key server:
gpg --keyid-format long --keyserver keys.openpgp.org --recv-keys 5069A233D55A0EEB174A5FC3821ACD02680D16DEWhich should produce the following output:
gpg: key 821ACD02680D16DE: public key "VeraCrypt Team (2018 - Supersedes Key ID=0x54DDD393) <veracrypt@idrix.fr>" imported
gpg: Total number processed: 1
gpg: imported: 1This message tells us that we have successfully imported the key which we can use to verify the signature of the installer. Furthermore we see the expected VeraCrypt email being associated with it.
It is highly unlikely (“impossible”) that an intruder could have hacked both the VeraCrypt download page and the trusted public key server to inject his faux installer and keys, but even though everything “seems to be in order”, we are still blindly trusting the OpenPGP public key server and that it is providing us with the true public key of VeraCrypt. We have not done any verification of the public key on our end. If this trust is a bit more than what you’re comfortable with you can of course ultimately verify the authenticity of the public key you just imported. Google will have to help you out with the exact details, though.
Accepting the unverified authenticity of the OpenPGP public key server, we can retry the verification command on the installer again, which this time will produce a different message:
gpg: Signature made sun 27 okt 2019 18:54:11 CET
gpg: using RSA key 5069A233D55A0EEB174A5FC3821ACD02680D16DE
gpg: Good signature from "VeraCrypt Team (2018 - Supersedes Key ID=0x54DDD393) <veracrypt@idrix.fr>" [unknown]
gpg: WARNING: This key is not certified with a trusted signature!
gpg: There is no indication that the signature belongs to the owner.
Primary key fingerprint: 5069 A233 D55A 0EEB 174A 5FC3 821A CD02 680D 16DEBy default imported public keys will not have an ultimate trust level in your keychain, hence the WARNING part, but we choose to accept this for now. Again; if you do not want to accept it you’ll have to ultimately verify the public key.
What is more interesting is the Good signature part. If present, it basically says that it is mathematically guaranteed that the target file, in our case the VeraCrypt installer, was signed by the owner of the public key we verified it against.
All good so far. We will now proceed with verifying the integrity of the downloaded SHA-256 and SHA-512 checksums files in the same way:
gpg --keyid-format long --verify <sha-checksums-signature> <sha-checksums-file>Observe how they both produce the same Good signature output as the installer verification did.
Next step is to calculate the SHA-256 and/or SHA-512 checksums of the installer and compare it to an expected reference value in the now verified checksums file. The SHA checksum verification step is not necessarily part of the actual authenticity/integrity verification, but rather to ensure that the download itself went well and that we didn’t lose any packets.
sha256sum -c veracrypt-1.24-Hotfix1-sha256sum.txt 2>&1 | grep OKExecuting the above command on a recent Ubuntu distribution should produce the following output (you may have to save the “txt” file with Unix or Mac style line breaks first, depending on your system):
veracrypt-1.24-Hotfix1-Ubuntu-19.10-amd64.deb: OKAll good? Go ahead and install the downloaded binary as of normal procedures for your platform, and know that you safely can proceed securing your USB stick.
No good? Then there might be a typo somewhere or something isn’t right with the published install file. If you suspect the installer has been tampered with, you should reach out to the VeraCrypt team for further instructions.
Final nitpicking notes: If you check the links of the six downloaded files you will notice that they all seem to be coming from the same source, which is a bit unfortunate. It would have added significant complexity for a hacker if he would have had to hack ultimately six + one servers (one for each downloaded file + the trusted and secured key server) in a desperate attempt of attack.
Prepare the USB drive
VeraCrypt can create at least two different types of secure containers:
- A “secure container” which, in all practical matters, is just a file on your file system. You can copy it, move it to the cloud, or even delete it without compromising the security.
- A partition of your disk (e.g. your USB drive). These are handled as regular disk volumes, but encrypted.
In this write-up we will choose the latter approach.
Setup a secured volume on the USB
What VeraCrypt will do for us is to create an outer volume on our USB drive. This volume will act as a “fake” secure container. However, since we are sneaky devils, we will ask VeraCrypt to also create another, hidden, and also encrypted inner volume, which will be where we store our actual secrets. This way, if we find ourselves in a situation where the encryption password is forced of our hands, we can safely expose our outer volume by giving away our “outer password” but still keep our secrets intact in the inner volume, which is encrypted with a different password.
This hiding will work mathematically as well because VeraCrypt always writes random data to the unused parts of a volume. Due to mathematical properties of the encryption algorithm, the encrypted data looks exactly like random data. Examining the raw bytes of the volume, which is what a hacker would have to resort to, one can not see any difference between the encrypted and randomised parts of the volume. Without the encryption password, which could be any combination of (theoretically) any number of characters in the world, one can not even begin to try decrypting or guessing the content.
The below pictures show how the hiding works:
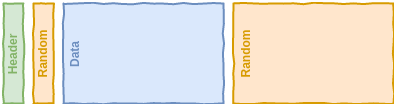

You can (and should) even generate a set of fake copies of some seemingly important files and put them in this outer volume to seem even more credible. More on this later.
Create the fake, outer volume
So let’s get to it, shall we?
- Start VeraCrypt and select an empty slot in the list and click the “Create Volume” button.
- Next, choose the “Create a volume within a partition/drive” option.
- And then choose “Hidden VeraCrypt volume”. It is highly recommended to read the information given in the UI, it is surprisingly informative.
- In the next view you have to locate your USB drive.
- Next up, you will see a summary of exactly what is about to happen. Make sure you read and understand the info before clicking the “Yes” button.
- Next step is to choose your encryption options for the outer volume. Choosing
Serpent(Twofish(AES))andSHA-512will make sure God himself would have to break sweat before cracking the encryption. - Next, choose an encryption password for the outer volume. Even though this is the “fake container”, you still need to remember this password as this is the one you’d give to a potential extortioner (write it down on a piece of paper). Follow the on-screen instructions and click the “Format” button when ready.
That is our fake, outer volume. Now go on, follow the instructions on the screen and create some fake content in the outer volume (note the “Open volume” button).
It is worth to mention that this is probably the safest point in time when you can add the fake content, so don’t skip it!
Creating the hidden, inner volume
We will now create our real secured container, where we will hide all our gold:
- Continuing from the previous view, choose the encryption details for the inner volume.
Serpent(Twofish(AES))andSHA-512seems like reasonable choices. - Next, choose a maximum size for the inner volume. Except for the physical limitations of your USB stick, your needs are the only determining factor here. Click “Next” when done.
- Now you’ll choose an encryption password for the inner volume. Recommendation here is to generate the most complex password that is accepted by VeraCrypt and to keep it in your password manager. It must be completely different from the outer password.
- Next up you’ll choose the filesystem format of your inner volume. Though not the most efficient, FAT file systems will play along with most (all?) operating systems out there. Choose as you wish here.
- Next, re-generate the entropy for the cryptographic random number generator and click “Format” when done.
Once this format operation is finished we are done! Click the “Exit” button and go have a beer, you have earned it!
Accessing the hidden, inner volume
When you wish to read or write data on the hidden volume on the secured USB you follow the same mount pattern as you would do for a non-hidden volume:
- Start VeraCrypt and select an empty slot in the list.
- Click the “Select Device” button and, well, select your USB drive.
- Click the “Mount” button and enter the password for your hidden inner volume.
- When mounted, double click the selected slot to open the file browser.
The important part here is to enter the password for the inner volume when mounting your secured USB by your own free will. VeraCrypt will decrypt and mount the inner or the outer volume depending on which password you enter.
If you enter the password for the outer volume you will mount the “fake container”, which is exactly what you want to do when forced. But be aware that you may risk corrupting your hidden volume if you start writing large amounts of (fake) data to this container.
All information above, and much, much more can be found in the official VeraCrypt documentation pages.
Credits
MILKOVÍCheat-sheet
Below you will find the “no-talking-only-doing” instructions for setting things up. Some intermediate steps are for you to realise and act on.
Download, verify and install
- Download VeraCrypt install and checksum files:
https://www.veracrypt.fr/en/Downloads.html - Verify integrity of installer (will fail due to missing key):
gpg --keyid-format long --verify <signature> <installer> - Import key:
gpg --keyid-format long --keyserver keys.openpgp.org --recv-keys <fingerprint> - Verify integrity of installer (again, should succeed):
gpg --keyid-format long --verify <signature> <installer> - Verify integrity of checksums file(s):
gpg --keyid-format long --verify <signature> <checksums> - Verify SHA checksum of installer:
sha256sum -c <sha256_checksums> 2>&1 | grep OKsha512sum -c <sha512_checksums> 2>&1 | grep OK
Create hidden volume
- Start VeraCrypt, select empty slot, click “Create Volume” button
- Choose “Create a volume within a partition/drive”
- Choose “Hidden VeraCrypt volume”
- Select
Serpent(Twofish(AES))encryption andSHA-512hashing for the outer volume - Generate secure, random password for outer volume
- Add “fake” content
- Select
Serpent(Twofish(AES))encryption andSHA-512hashing for the inner volume - Enter reasonable size of inner volume
- Generate secure, random password for inner volume
- Pick a file system format for the inner volume
Access hidden data
- Start VeraCrypt and select empty slot
- Click “Mount Device” button
- Click “Mount” button and enter password for inner volume
- Double-click the selected slot for opening file browser
